Getting Started with Trezor: Your Complete Crypto Security Guide
A step-by-step guide to safely managing your cryptocurrencies with Trezor hardware wallets.
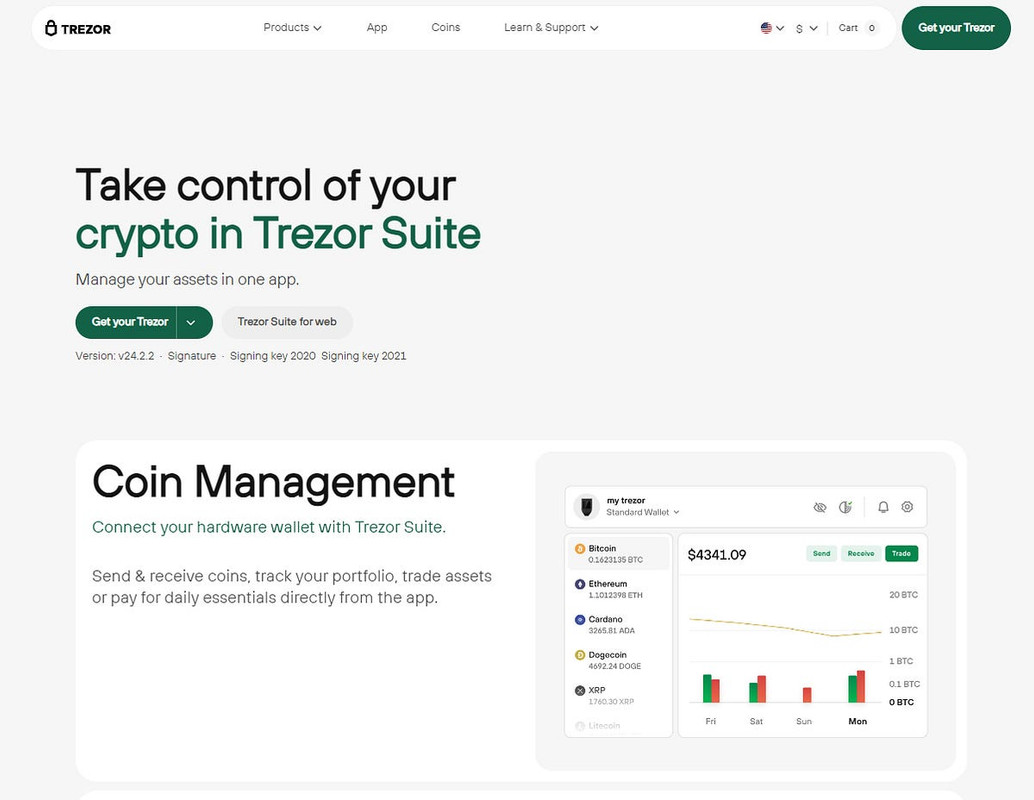
Why a Hardware Wallet Matters
For beginners stepping into the crypto world, security can seem overwhelming. Unlike exchanges or software wallets, hardware wallets like Trezor store your private keys offline. This means your digital assets remain protected from online attacks, phishing attempts, and malware.
Imagine your crypto as cash in a safe. Trezor is that high-tech, tamper-proof safe, giving you peace of mind.
Step 1: Purchase and Unbox Your Trezor
Head to trezor.io/start to order the official Trezor device. Avoid third-party sellers to minimize risks of tampered devices. Once delivered, unbox it carefully, ensuring all security seals are intact.
Step 2: Initialize Your Wallet
Connect your Trezor to your computer and follow the setup guide on the official site. During initialization, you'll:
- Create a secure PIN
- Generate your recovery seed
- Confirm the seed to ensure you’ve recorded it accurately
This recovery seed is your lifeline. Store it offline in a safe location. Losing it can mean losing access to your funds forever.
Step 3: Adding Cryptocurrencies
Trezor supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, and many altcoins. You can:
- Open the Trezor Suite app or web interface
- Select your preferred cryptocurrency
- Generate a receiving address
- Transfer funds from exchanges or other wallets
Always double-check addresses and transaction details. A single typo can lead to permanent loss.
Security Best Practices
While Trezor provides robust protection, user habits matter too. Follow these tips:
- Never share your recovery seed or PIN.
- Keep your firmware updated to the latest version.
- Use a strong, unique password for Trezor Suite accounts.
- Consider storing your device in a secure, tamper-proof location when not in use.
Think of your Trezor as a vault. Even the best vault is useless if you leave the key under the doormat.
Comparison: Trezor vs. Software Wallets
| Feature | Trezor | Software Wallet |
|---|---|---|
| Private Key Storage | Offline | Online |
| Security Against Hacks | Very High | Moderate |
| Ease of Use | Moderate | High |
| Cost | Paid Device | Free |
FAQs About Trezor
Yes, using the recovery seed you set up during initialization.
Q2: Does Trezor support Ethereum and ERC-20 tokens?Absolutely. Trezor supports multiple cryptocurrencies and tokens via the Trezor Suite.
Q3: Is it safe to connect Trezor to public computers?It’s not recommended. Always use trusted devices to prevent potential malware attacks.
Conclusion: Secure Your Crypto Journey
Trezor provides an essential layer of security for anyone serious about cryptocurrency. By combining offline key storage, easy setup, and compatibility with multiple crypto assets, it empowers users to confidently manage their digital wealth. Start today at trezor.io/start and take control of your crypto security with a hardware wallet that’s trusted worldwide.